Overview
Sophisticated yet simple security for your desktop environment.
Sophos Endpoint Protection makes it simple to secure your Windows, Mac and Linux systems against malware and advanced threats, such as targeted attacks.
Sophos' next generation endpoint protection integrates innovative technology like malicious traffic detection with real-time threat intelligence from SophosLabs to help you prevent, detect and remediate threats with ease. Web, application, and peripheral access policies can follow your users anywhere they go. And, your firewall and endpoints can share a security heartbeat.
EndPoint Features
Endpoint Detection and Response (EDR)
Automatically detect and prioritize potential threats and quickly see where to focus attention and know which machines may be impacted.
Sophos Intercept X Advanced with XDR integrates powerful endpoint detection and response (EDR) with the industry’s top-rated endpoint protection. Built for both IT security operations and threat hunting, Intercept X detects and investigates suspicious activity with AI-driven analysis. Unlike other EDR tools, it adds expertise, not headcount by replicating the skills of hard-to-find analysts.
Extended Detection and Response (XDR)
Go beyond the endpoint by incorporating cross-product data sources for even more visibility
Sophos Intercept X Advanced with XDR integrates network, email, cloud*, and mobile* data sources on top of endpoint and server information, giving you an even broader of your organization’s cybersecurity posture. With 30 days of cloud storage included you can look back in time to understand how an attempted breach began and conduct real-time investigations
Anti-Ransomware
Ransomware file protection, automatic file recovery, and behavioral analysis to stop ransomware and boot record attacks
Today’s ransomware attacks often combine multiple advanced techniques with real-time hacking. To minimize your risk of falling victim you need advanced protection that monitors and secures the whole attack chain. Sophos Intercept X gives you advanced protection technologies that disrupt the whole attack chain including deep learning that predictively prevents attacks, and CryptoGuard which rolls back the unauthorized encryption of files in seconds.
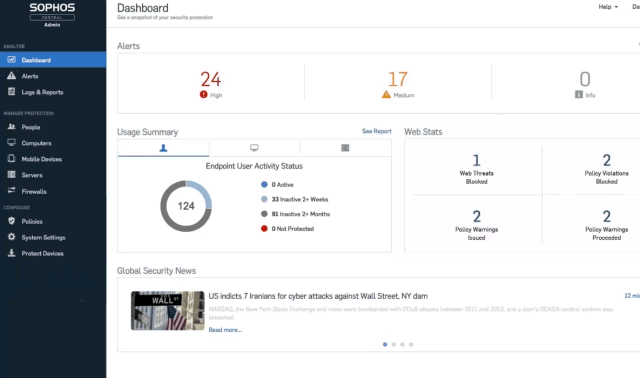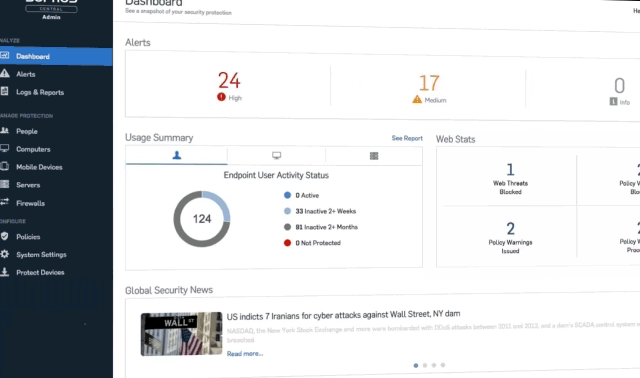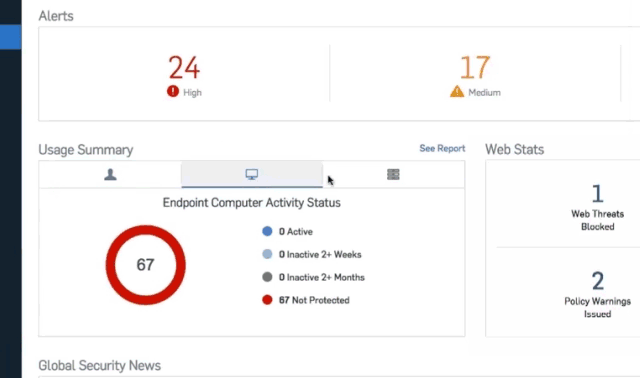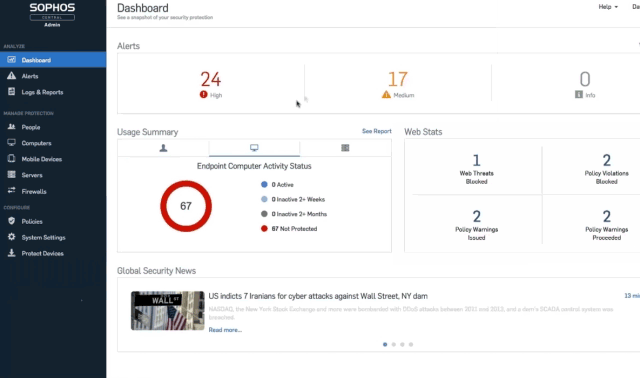
Simple security for your business
- Protect all your devices: Innovative protection including anti-malware, HIPS and malicious traffic detection
- One simplified management console: Choose cloud-based Sophos Central or deploy Sophos Enterprise Console to manage your deployment
- On-premises or in the cloud: Choose from an on-premises solution, or one hosted in the cloud.
Deep Learning Technology
Artificial intelligence built into Intercept X that detects both known and unknown malware without relying on signatures
By integrating deep learning, an advanced form of machine learning, Intercept X is changing endpoint security from a reactive to a predictive approach to protect against both known and never-seen-before threats. While many products claim to use machine learning, not all machine learning is created equally. Deep learning has consistently outperformed other machine learning models for malware detection.
Exploit Prevention
Deny attackers by blocking the exploits and techniques used to distribute malware, steal credentials, and escape detection
Exploit prevention stops the techniques used in file-less, malware-less, and exploit-based attacks. While there are millions of pieces of malware in existence, and thousands of software vulnerabilities waiting to be exploited, there are only handful of exploit techniques attackers rely on as part of the attack chain – and by taking away the key tools hackers love to use, Intercept X stops zero-day attacks before they can get started.
Managed Threat Response
Elite team of threat hunters and response experts who take targeted actions on your behalf to neutralize even the most sophisticated threats
Sophos Managed Threat Response (MTR) provides 24/7 threat hunting, detection, and response capabilities delivered by an expert team as a fully-managed service. Sophos MTR fuses machine learning technology and expert analysis for improved threat hunting and detection, deeper investigation of alerts, and targeted actions to eliminate threats with speed and precision. Unlike other services, the Sophos MTR team goes beyond simply notifying you of attacks or suspicious behaviors, and takes targeted actions on your behalf to neutralize even the most sophisticated and complex threats.
Active Adversary Mitigations
Active adversary mitigation prevents persistence on machines, credential theft protection, and malicious traffic detection
Intercept X utilizes a range of techniques, including credential theft prevention, code cave utilization detection, and APC protection that attackers use to gain a presence and remain undetected on victim networks. As attackers have increasingly focused on techniques beyond malware in order to move around systems and networks as a legitimate user, Intercept X detects and prevents this behavior in order to prevent attackers from completing their mission.
Central Management
Manage your endpoint protection, EDR, XDR and other Sophos solutions from a unified console
Sophos Central is the cloud-based management platform for all Sophos solutions. You can investigate potential threats, create and deploy policies, manage your estate, see what is installed where and more, all from the same unified console.
Synchronized Security
Sophos solutions automatically share data and take response actions
Sophos solutions work better together. For example, Intercept X and Sophos Firewall will coordinate to identify, isolate and cleanup devices that have been compromised. When the threat is neutralized and there is no risk of lateral movement, network connectivity is restored. It all happens automatically with no admin intervention required.
Innovative protection
Sophos Endpoint Protection goes far beyond signature-based prevention of known malware, or being a simple web filter. It correlates suspicious behaviors and activities using real-time threat
intelligence from SophosLabs. From malicious URLs to web exploit code, unexpected system changes to command-and-control traffic, we’ll connect the dots so your
endpoints and data are protected. The result is fewer infected computers and better protection against targeted attacks and data breaches.
Complete control
Enforce your web, application, device and data policies with ease, thanks to seamless integration within the endpoint agent and the management console.
- Web Control Category-based web filtering enforced on and off the corporate network
- Application Control Point-and-click blocking of applications by category or name
- Peripheral Control Managed access to removable media and mobile devices
- Data Loss Prevention (DLP) Restrict unauthorized data flow using prebuilt or custom rules
Lightning performance
Sophos Endpoint Protection is continually tuned for the best performance. The lightweight agent keeps users secure without slowing them down. Protection updates
are small - typically under 30 KB - so updates are easy on your network and your endpoints.
"We have found the Sophos endpoint solutions to be easy, smooth and consistent. Having Sophos deployed has increased our security posture ten-fold."
Christopher Prewitt, Manager IT Security and Disaster Recovery, The Lincoln Electric Co.